Security Fuse Box Explained Identify Fuses and Troubleshoot Electrical Problems security considerations for deploying notes plugins
If you are looking for Security and the Right to Security – Gentil Kasongo you've visit to the right place. We have 25 Pictures about Security and the Right to Security – Gentil Kasongo like National Retail's Timely Collaboration with Ignite Systems Amidst Cyber, Ai Used In Cybersecurity and also AI in Cybersecurity: Opportunities & Challenges | Techgenies. Here you go:
Security And The Right To Security – Gentil Kasongo
 gentilkasongo.com
gentilkasongo.com
Security and the Right to Security – Gentil Kasongo
Use An Air Gap For Security | SlawTips
 tips.slaw.ca
tips.slaw.ca
Use an Air Gap for Security | SlawTips
Millennials Want The Security Of Their Own Roof Over Their Heads
 www.businessoutreach.in
www.businessoutreach.in
Millennials want the security of their own roof over their heads
Australian Security - Australian Security - Medium
 medium.com
medium.com
Australian Security - Australian Security - Medium
Cybersecurity Plan: 3 Keys For CISOs - Rushhourtimes.com
 rushhourtimes.com
rushhourtimes.com
Cybersecurity plan: 3 keys for CISOs - rushhourtimes.com
Cybersecurity - Tunya Systems Limited
 tunyasystems.co.ke
tunyasystems.co.ke
Cybersecurity - Tunya Systems Limited
Security Considerations For Deploying Notes Plugins
 www.bcchub.com
www.bcchub.com
Security Considerations for Deploying Notes Plugins
Cyber Security Hd Background, Cyber Security Wallpaper, Cyber Security
 stock.adobe.com
stock.adobe.com
cyber security hd background, cyber security wallpaper, cyber security ...
The Sony Pictures Hack And Learning Information Security Lessons The
The Sony Pictures Hack and Learning Information Security Lessons the ...
5 Security Measures That Experts Follow (and So Should You!) - Panda
 www.pandasecurity.com
www.pandasecurity.com
5 security measures that experts follow (and so should you!) - Panda ...
1000x2000 Resolution Cybersecurity Core 1000x2000 Resolution Wallpaper
 wallpapersden.com
wallpapersden.com
1000x2000 Resolution Cybersecurity Core 1000x2000 Resolution Wallpaper ...
AI In Cybersecurity: Opportunities & Challenges | Techgenies
 techgenies.com
techgenies.com
AI in Cybersecurity: Opportunities & Challenges | Techgenies
Cyber Security For OT - AutomaTech
 automatech.com
automatech.com
Cyber Security for OT - AutomaTech
How To Maintain Business Security When You’re Not There? – AtulHost
 www.atulhost.com
www.atulhost.com
How to maintain business security when you’re not there? – AtulHost
The Major Concern Of Every Person Has To Be Their Security - Ivy
 ivycastellanos.com
ivycastellanos.com
The major concern of every person has to be their security - Ivy ...
CloudBric: The Future Of Cloud Computing And Cyber Security. | By Carl
 medium.datadriveninvestor.com
medium.datadriveninvestor.com
CloudBric: The Future of Cloud Computing and Cyber Security. | by Carl ...
Bolstering Cybersecurity Readiness In The Cloud - Information Age
 www.information-age.com
www.information-age.com
Bolstering cybersecurity readiness in the cloud - Information Age
Cyber Security In Software Development: 12 Outsourcing Tips
 senlainc.com
senlainc.com
Cyber security in software development: 12 outsourcing tips
¿Qué Es Una Auditoría De Seguridad Cibernética Y Por Qué Es Importante
 easydmarc.com
easydmarc.com
¿Qué es una auditoría de seguridad cibernética y por qué es importante ...
What Is Cybersecurity? A Complete Overview Guide
 www.springboard.com
www.springboard.com
What Is Cybersecurity? A Complete Overview Guide
What Is Cybersecurity Risk Management? Implementation Guide
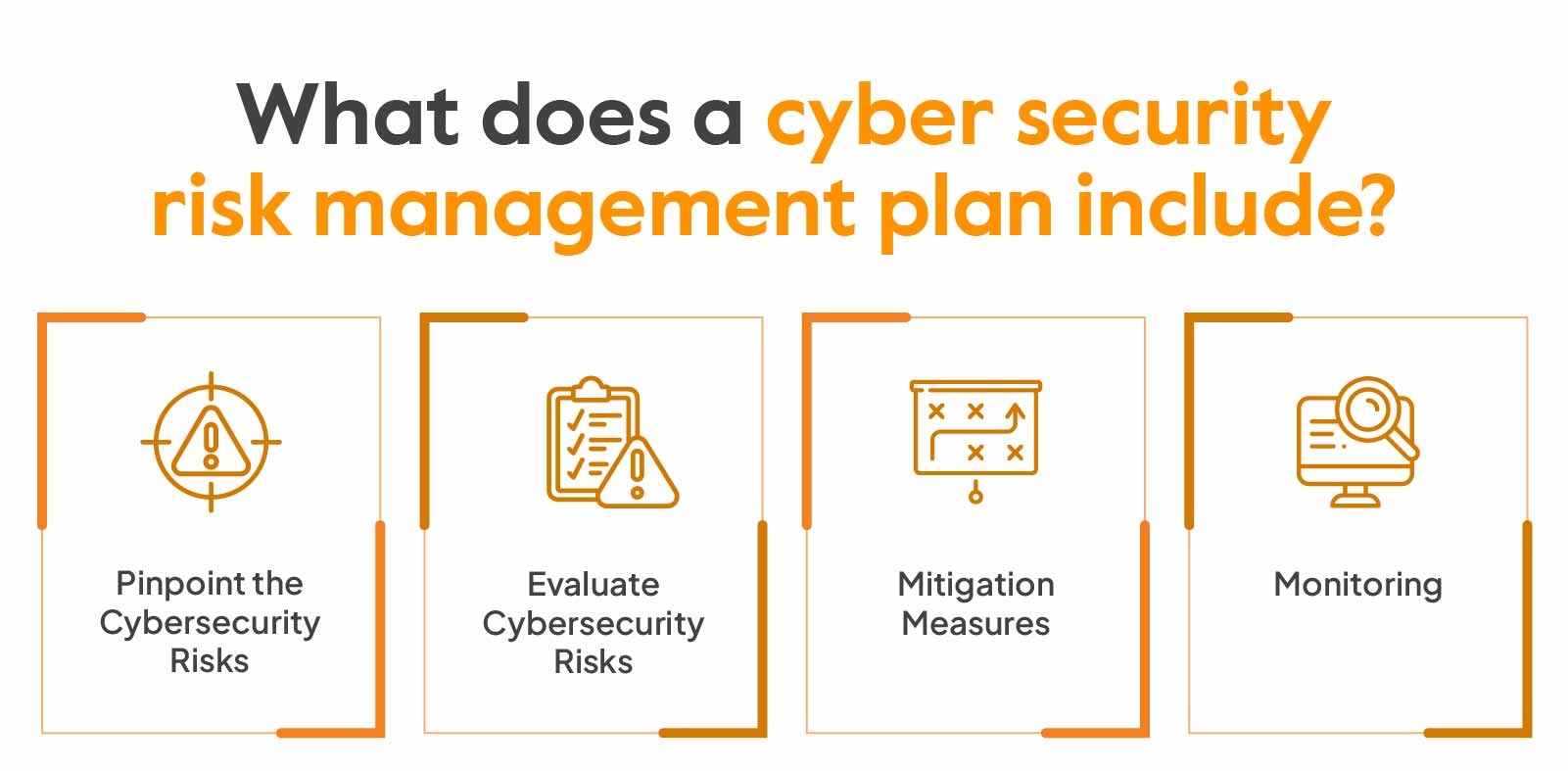 sprinto.com
sprinto.com
What is Cybersecurity Risk Management? Implementation Guide
What Is Manned Guarding In The Security Industry
 www.kingdom.co.uk
www.kingdom.co.uk
What is manned guarding in the security industry
Ai Used In Cybersecurity
 daliminatorxkj1study.z21.web.core.windows.net
daliminatorxkj1study.z21.web.core.windows.net
Ai Used In Cybersecurity
[100+] Security Wallpapers | Wallpapers.com
![[100+] Security Wallpapers | Wallpapers.com](https://wallpapers.com/images/hd/cool-cyber-security-illustration-0pfgwic7nwcaeeym.jpg) wallpapers.com
wallpapers.com
[100+] Security Wallpapers | Wallpapers.com
National Retail's Timely Collaboration With Ignite Systems Amidst Cyber
 www.nationalretail.org.au
www.nationalretail.org.au
National Retail's Timely Collaboration with Ignite Systems Amidst Cyber ...
1000x2000 resolution cybersecurity core 1000x2000 resolution wallpaper .... What is cybersecurity risk management? implementation guide. How to maintain business security when you’re not there? – atulhost